WEB
The internet is a massive network of networks, and it connects millions of computers together globally, forming a superset in which any computer can communicate with any other connected with any other computer as long as they are both connected to the Internet.
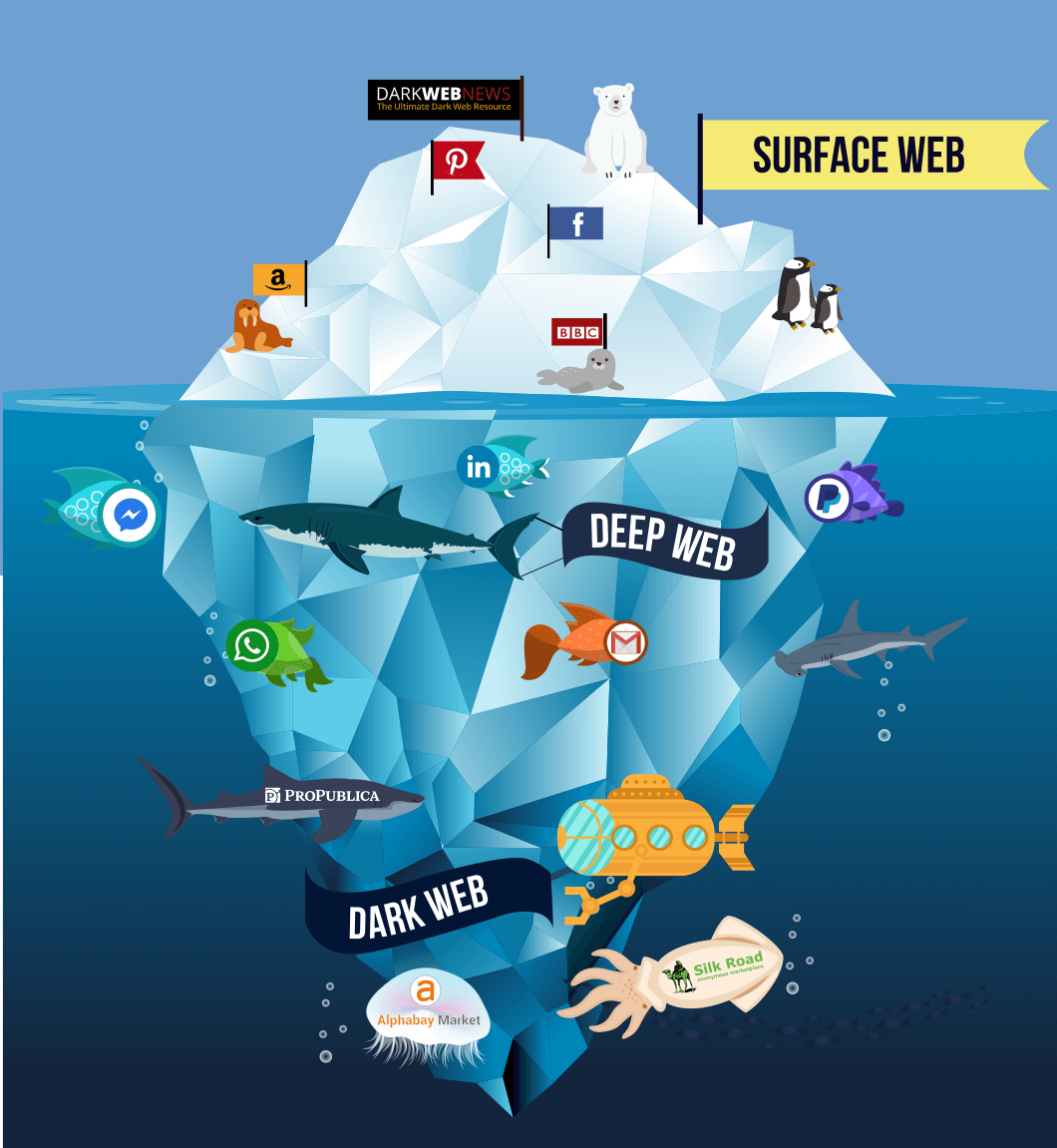
Many people like to view the internet as an island or a glacier at sea, and only part of it is viewable above the surface of the water.
Two Basic Content Categories of WWW
Structured and Unstructured, while the web consists of several layers of accessibility.
Clear Web or Surface Web
Surface web is the portion of the web that is readily available to the public and searchable with standard web search engines (eg., mozilla, opera, google, bing, yahoo, edge, etc) index sites whose domain end in .com, .org, .net or similar variations and whose content does not need any special configuration to access.
It is actually only a small part of the entire internet. It contains all the publicaly available information, documents, and content.
The Deep Web
Most of the people never heard about them and they view as the same thing, which is as a depraved and illegal area on the internet. It is estimated that 90% of all internet data and websites are hidden from search engine indexing, this area of the internet is known as Deep Web.
The Deep Web is the area on the internet that can't be, or isn't indexed because the deep web includes much more than what you probably think. any website or system that needs login credentials is part of the deep web.
The deep web is accessible using any standard browser, but is not indexed by search engines, so you usually need to either enter a username and password to access the content or be in a specific network(like company, college network, ..) then there is another section which is sub-set of the deep web i.e., dark web that consists of sites about drugs, pornography, weapons, counterfeit, hacking, etc...
The Dark web
As the Surface Web, or WWW, is on the internet, the Dark Web exists on the Dark Net(or rather, multiple darknets).
Dark Net and Dark Web aren't the same thing. Dark Net are the networks that were isolated from ARPANET, mainly for security purposes, such as compartmentalization. They were configured to be able to receive external data, but they were hidden from ARPANET network listings and wouldn't respond to networking process, such as ping request. an example of dark net is TOR or The Onion Router. It's essentially a distributed networks of servers or hosts, where users, traffic is bounced around between various routers.
TOR
To protect yourself while browsing the internet you should be using TOR which stands for The Onion Router. TOR will provide you with a degree of anonymity by using an 128-bit AES (Advanced Encryption Standard) To browse the .onion links, you need Tor. Tor (The Onion Router) is an free open-source software designed for anonymous, uncensored communication. The website you visit using the TOR browser can load much longer due to the route the connection has to take.
How to access TOR?
The easiest way to access Tor is to install Tor Browser. It is available for Windows, Linux, OS X and Android.
Download the TOR Browser
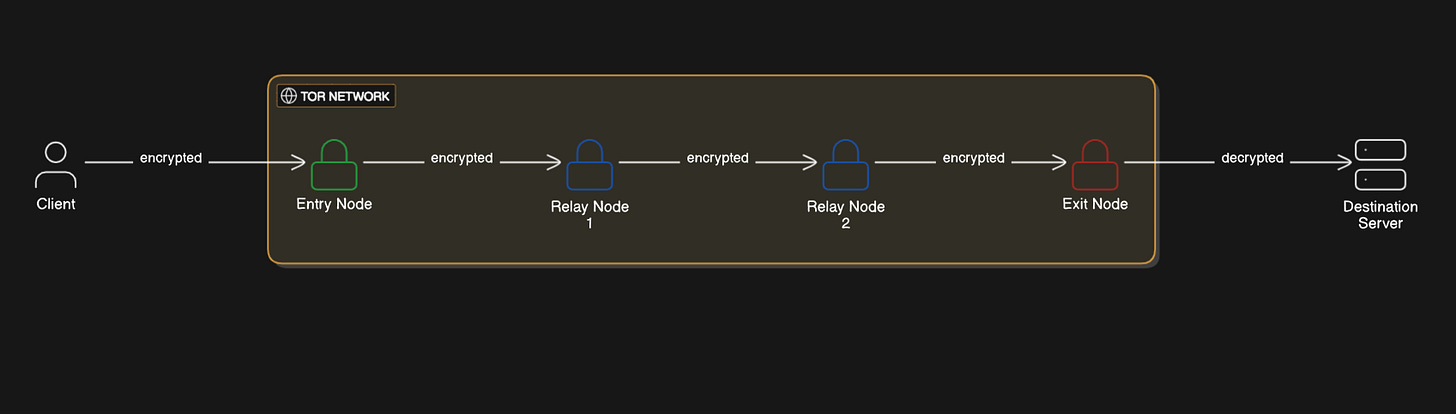
How does TOR work?
Your traffic passes through at least 3 different servers before sending it on to the destination. Because each of the 3 nodes has separate layer of encryption, nobody watching your connection can read what you are sending into Tor network.
The nodes are called
Guard node Knows your IP address but doesn't know where you are connecting to
Middle node Immediate layer between guard node and exit node.
Exit node Knows the destination but doesn't know who you are.
How to use VPN?
using a VPN along with TOR, you can add an extra layer of encryption and anonymity making it virtually impossible to trace.
This site that tests and rates VPN's used for TOR :
Safety settings
The TOR browser offers three levels of user protection: safest, standard, and safer.
Safer: disables potentially dangerous functions of websites. some fonts or symbols may not work properly and multimedia such as audio and video clips only start with a click. Furthermore, java scripts are disabled on all non- HTTPS pages.
Standard: all functions of the browser and websites are enabled, this guarantees full functionality of the websites. Use the standard settings only when browsing known, trusted sites.
Safest: allows websites to use only their basic functions. Scripts on all pages, even those with HTTPS protocol do not start. Many pages will be non-functional in this mode.
Why Dark Web?
For Privacy
Nowadays, Internet privacy is a joke. Privacy is a top concern for many people today. With the rise of interconnected devices and data being moved to the cloud, privacy concerns are on the rise
When you browse an average website, There are a number of tracking actions that the website can perform. for instance:
Tracking cookies
Referral links
IP addresses
Tracking scripts
Fingerprinting of the browser
using the information obtained, websites can perform a few things, such as targeted advertising.
By using the dark web, people ensure that they are keeping their legal online activity anonymous. There is no need to worry about websites tracking your location or online activity.
if you want the best anonymity then it tough to beat the tor browser. The best option to stay private most of the time.
gaining access to the dark web. there is more things going on in the dark web. so tread lightly if you venture there because you could end up in trouble with law.
you'll be practically invisible to prying eyes.
the tor is a golden standard if you want to browse in private. It is highly mobile and allows for access to be carefully hidden.
Some Tips to remain Anonymous
Do not give out any real data or any information that could lead to your identity.
Do not use the browser in full screen mode.
When using the forums, use a nickname you've never used before.
Use the Safest TOR browser mode while browsing websites.
When using the TOR network, do not log into your real accounts on any sites such as facebook, Instagram, etc.
Do not install any additional browser extensions.
Some Onion Websites:
Here, I will not suggest any website because I don’t trust any of them. Just go through your way.
Is Tor legal?
In most countries using Tor is legal. However, some countries censor Internet and the only way to access Tor is to use a bridge. In this case select "Tor is censored in my country" in connection wizard after starting Tor Browser. You may also set up bridge in settings.
Sites within the TOR network are not always maintained or as long-lasting as those outside of the network.
Note: We do not encourage or condone any illegal activity, this is for only mere educational purposes.
Conclusion
Tor (The Onion Router) is a decentralised anonymity network that uses a distributed relay system to route traffic, allowing users to browse and communicate privately. Working with Tor as a developer gives you the chance to support digital rights while navigating the moral and technical challenges of privacy technology. Its architecture puts decentralised anonymity above speed and is based on volunteer-operated nodes, multilayer encryption (hence "onion" routing). Tor's protocols can be integrated by developers to create privacy-focused apps, host censorship-resistant .onion services, or contribute to the network itself by running relays or improving its open-source codebase.
Thanks for reading this article.
If you’ve made it this far, congrats!
See you in the next blog, Until then keep developing and solving.
Want to connect? Send me a direct message on X,
If you're curious or have any questions on the subject; I'd be pleased to chat with you!